In this blog we explain how you can gain insight into the current status of your organization's cybersecurity and how you can improve it. In addition, we share more about Sentinel and the MITRE ATT&CK Framework, what attack vectors from hacker groups are and how CloudNation brings this together to give organizations insight into their cyber resilience.
SIEM, SOAR and Sentinel
Sentinel occupies a prominent place within Azure's extensive security suite. Not only does it function as a Security Information and Event Management (SIEM) solution, but it is also a Security Orchestration, Automation, and Response (SOAR) platform. Sentinel therefore offers the possibility to aggregate data from the Azure environment, on-premises, and various cloud environments. It enables organizations to develop use cases, generate alerts, and write playbooks for automated incident response.
MITRE ATT&CK Framework
The MITRE ATT&CK Framework is an open source framework that is used to identify hackers at a point in the “killchain” where they are with their attack.
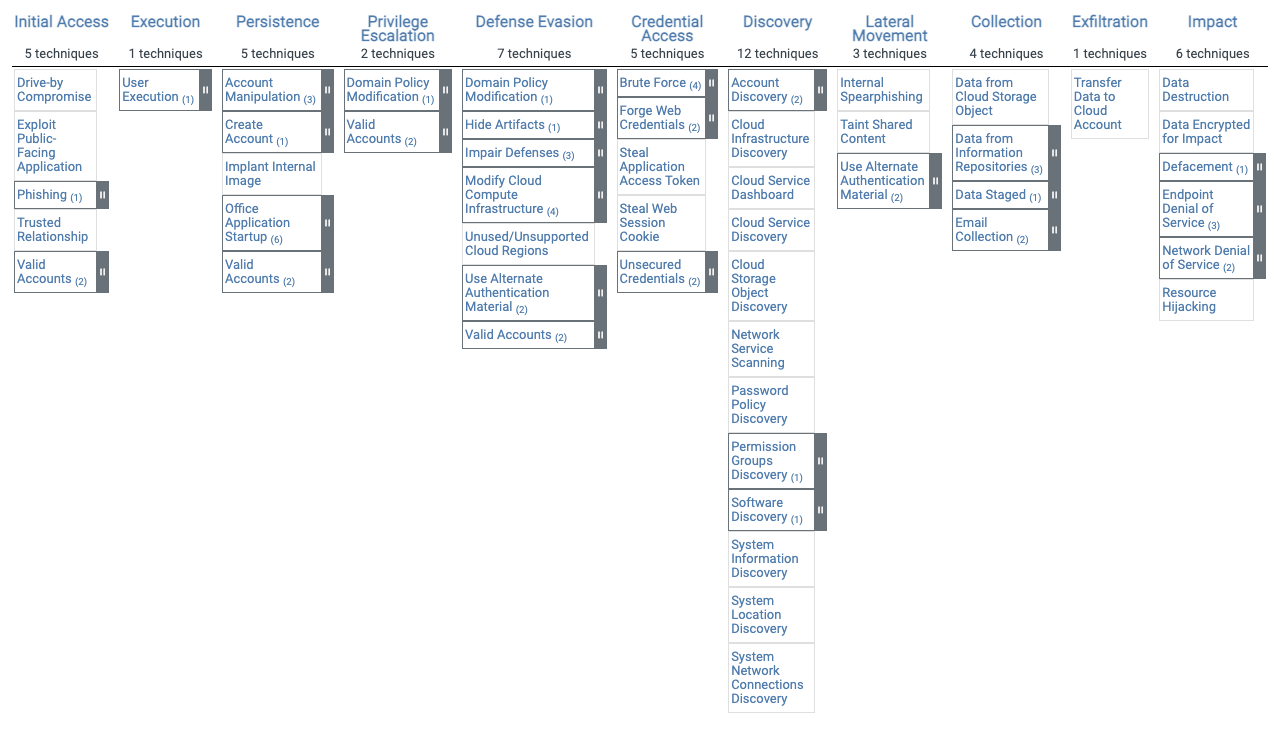
The image should be read from left to right and from top to bottom. An attacker from a specific group can follow a defined attack path, which moves from left to right. With regard to the costs for mitigation, it is lowest for the consequences. If an attacker is located further to the right in the framework, the costs for mitigation increase.
This principle occurs as follows: Under the heading "Initial Access" it is indicated that phishing is one of the methods. To prevent a phishing attack, an organization can take the risk by performing both technical and non-technical activities. The cost of preventing a phishing attack is significantly lower than the costs resulting from the consequences of data collection.
Synergy between Sentinel and MITRE ATT&CK
When creating use cases in Sentinel it is possible to integrate the MITRE ATT&CK Framework by adding the unique MITRE T-number. This will include the use case in the coverage overview, as illustrated in the example below.

Here, the darker the tile, the more use cases with that subtechnique are present in Sentinel. However, this does not provide a clear picture of the specific attack vector used by certain hacker groups. MITRE ATT&CK provides a list of known hacker groups and their attack vectors, with an overlay that integrates with current defense techniques in Sentinel. This approach provides insight into the locations of attack vectors, reveals where current defenses are focused, and thus highlights areas of concern.
ActiveOne tooling
CloudNation help you gain insight into the current status of your cybersecurity through the implementation of the ActiveOne solution. This sets up the Defender suite of Microsoft Azure to meet compliance standards and best practices learned by experienced CloudNation consultants specialized in Governance and Security. The Security as Code deployment gives our customers the insight to determine the current situation, detect any blind spots and improve detection capabilities through use cases.
Furthermore, we vigilantly monitor attack groups to stay abreast of emerging threats.. Attacker groups use various methods depending on the specific sectors and industries. For example, attacking a company in the financial sector requires different attack techniques than in healthcare. MITRE ATT&CK provides an overview of these groups and their most commonly used attack techniques. By comparing the current situation with the most commonly used attack vector of these groups, a company gains insight into what it needs to pay more attention to.





